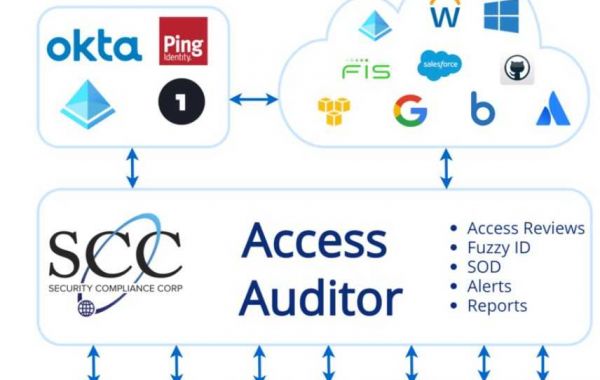
Introduction:
In an era marked by increasing cybersecurity threats and stringent regulatory requirements, organizations must adopt robust measures to safeguard sensitive data and ensure compliance with industry standards. One such measure is conducting regular user access reviews, which play a vital role in maintaining data security and adherence to regulatory mandates. In this comprehensive guide, we'll delve into the best practices for conducting user access reviews, highlighting their significance in bolstering data security and compliance within organizations.
The Significance of User Access Reviews:
User access reviews, also known as entitlement reviews or access recertification, involve evaluating and validating the permissions and privileges granted to users within an organization's IT systems and applications. These reviews are essential for several reasons:
- Data Security: User access reviews help mitigate security risks by identifying and remedying access-related vulnerabilities, such as excessive permissions, orphaned accounts, and unauthorized access attempts. By ensuring that users have the appropriate level of access required to perform their job duties effectively, organizations can minimize the risk of data breaches and insider threats.
- Compliance Adherence: Regulatory frameworks such as GDPR, HIPAA, PCI DSS, and SOX require organizations to implement robust access control mechanisms and regularly review user access rights to ensure compliance. User access reviews demonstrate an organization's commitment to safeguarding sensitive data and adhering to legal and regulatory requirements.
- Risk Management: By proactively identifying and addressing access-related risks, organizations can mitigate the potential impact of security incidents and data breaches. User access reviews enable organizations to assess and manage access controls effectively, reducing the likelihood of unauthorized access to critical systems and data.
Best Practices for Conducting User Access Reviews:
To maximize the effectiveness of user access reviews and achieve the desired outcomes of data security and compliance, organizations should adhere to the following best practices:
- Establish Clear Policies and Procedures:
- Define clear policies and procedures governing user access management, including the frequency, scope, and responsibilities for conducting access reviews.
- Document the review process, including the criteria for evaluating access rights, the roles and responsibilities of stakeholders involved, and the escalation procedures for addressing identified issues.
- Automate Review Processes:
- Leverage automated identity and access management (IAM) solutions to streamline the user access review process, improve accuracy, and reduce administrative overhead.
- Implement automated workflows for requesting, approving, and revoking access rights, ensuring that access controls are consistently enforced and auditable.
- Involve Stakeholders:
- Collaborate with business units, IT departments, compliance teams, and auditors to ensure that access reviews align with business requirements, regulatory obligations, and risk management objectives.
- Engage key stakeholders in the review process to solicit feedback, address concerns, and ensure that access decisions are based on business need and risk tolerance.
- Conduct Regular Reviews:
- Schedule regular access reviews at predefined intervals (e.g., quarterly, semi-annually, or annually) to maintain the integrity of access controls and address any changes in user roles or responsibilities.
- Use automated reminders and notifications to prompt stakeholders to complete their review tasks on time and escalate overdue reviews as necessary.
- Document Review Findings:
- Maintain comprehensive records of access review activities, including the rationale for access decisions, remediation actions taken, and evidence of compliance with regulatory requirements.
- Document any exceptions or deviations from established policies and procedures, along with the justification for granting or retaining access rights.
- Implement Segregation of Duties (SoD) Controls:
- Enforce segregation of duties to prevent conflicts of interest and unauthorized access by ensuring that no single user has the ability to perform incompatible actions that could lead to fraud or data manipulation.
- Identify and remediate any SoD violations identified during the access review process to mitigate the risk of fraud, errors, and compliance violations.
- Provide Training and Awareness:
- Educate users, managers, and administrators about the importance of access management, security best practices, and their role in safeguarding sensitive information.
- Offer training sessions, workshops, and online resources to raise awareness of security risks, regulatory requirements, and the importance of timely and accurate access reviews.
Conclusion:
User access reviews are a critical component of maintaining data security, mitigating risks, and ensuring compliance with regulatory requirements within organizations. By following best practices for conducting access reviews, organizations can strengthen their security posture, demonstrate accountability and transparency, and protect sensitive data from unauthorized access or misuse. By prioritizing user access reviews as a fundamental aspect of their cybersecurity and compliance programs, organizations can safeguard their reputation, preserve customer trust, and avoid the costly consequences of security breaches and compliance violations in today's rapidly evolving threat landscape.